Piglet from American Winnie the Pooh. Seven differences between the original Winnie the Pooh and the Russian one
The cryptocurrency boom of 2017 set a new direction for the creators of viruses, worms, Trojans and other malware.
Now they are not interested in your personal files and confidential data, but in the computing power of your device. The topic of today's article is mining viruses, how to recognize them and how to deal with them.
How to understand that your computer is infected with a miner
Mining programs load the processor or video card with complex mathematical calculations. Therefore, recognizing the presence of a malicious miner is in some sense much easier than in the case of a regular virus. Namely - due to the increased load on the computer.
Here's how it might manifest itself:

However, it is worth noting immediately that last method it doesn't always work. Only the most stupid and greedy miners load their equipment to full capacity, because then anyone will become suspicious. As a rule, mining viruses operate more subtly: they determine the processor (or video card) model and the number of cores, and occupy, for example, half or a third of the resources.
Moreover, some miners do not even appear in the Windows task manager and evade recognition by the load monitor. It turns out that you feel the load on the equipment, the fans are noisy, but the task manager reports that there is no load. In such cases, you can only get to the resource hog through a good antivirus. But such sophisticated miners are rare.
How to get rid of a miner manually
So, the easiest way to access the unsolicited miner is through the system monitor. But it’s better to use not a standard Windows monitor, but an advanced one - for example, Process Hacker. It sees hidden processes, tricks to hide the load do not help against it, and it has a lot of functions for managing processes.
Download the program from the official project website: . There is both an installer and a portable version that does not require installation. Launch the program and click on the “ CPU” to enable sorting processes by CPU consumption. A miner, even if it mercifully uses only half the processor, will immediately catch your eye.

In most cases, miner viruses are called something clever, trying to impersonate a system component or process of some harmless program. Don't let this bother you. Necessary and harmless processes do not load the system unless you ask them to do so. So you can safely begin neutralization.
Reflexively, hands reach out to complete the miner process, but there is no need to rush. First you need to find out where it is running from in order to remove it from the system forever. And to relieve the load, the process can simply be frozen. To do this, right-click on the process, and in the pop-up menu click “ Suspend”.

The miner will remain in memory, but will no longer be executed on the processor. Now you can interrogate him - in the same pop-up menu, click “ Properties" An information window about the process will open, where you will immediately see the path along which the miner is located.

All you have to do is follow this path and delete the folder with the miner using the combination Shift+Del, so that the folder does not fly into the trash, but is immediately erased from the drive.
Antivirus against miners
However, there is no need to fight mining viruses manually; antiviruses do an excellent job of dealing with them. This method is even better, because, as mentioned above, the miner can load the system in such a way that it is very difficult to notice - you will only wonder why everything slows down and jerks from time to time.
As an example, we consider here Avast- a very good antivirus that provides basic protective functions completely free of charge, without any trial periods. Go to the company's official website: download and install the program.
There is one caveat here. In general, antiviruses do not consider miners to be viruses, which is correct - miners do not damage your system and personal files, do not infect other computers, they simply use resources like any other program does. Therefore, in order for an antivirus to fight miners, you need to configure it so that it pays attention to potentially dangerous programs.
After starting Avast, click the “ Settings”, and on the “ tab Are common” (it will open first) check the boxes “ Enable enhanced mode" And " Look for potentially unwanted programs (PUPs)”.

Now on the “tab” Protection"click the button" Main protection components” and there activate all 3 available modules.

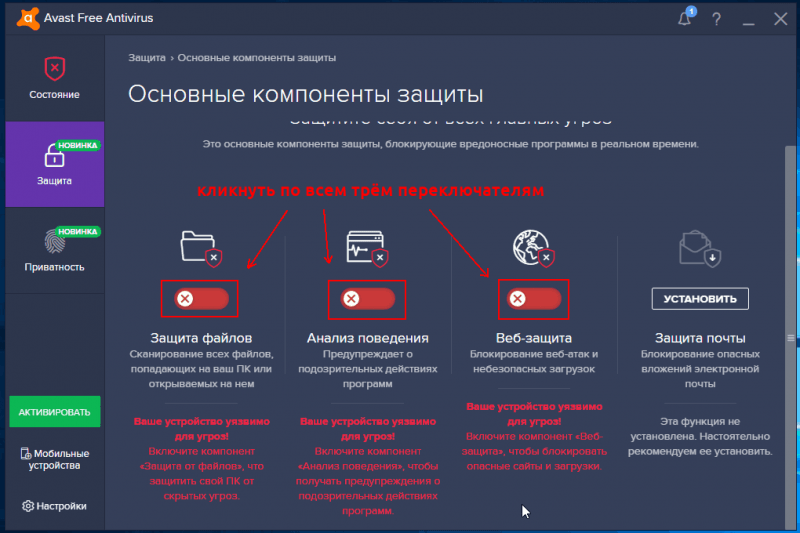
Wait 5-10 minutes and...

How to protect yourself from miner viruses
Treatment with antiviruses is a good thing, but it is better not to treat the infection, but to prevent it. Moreover, antiviruses, as a rule, do not keep up with the emergence of new varieties of computer infections.
The following rules will help you minimize the risk of infection and keep your computer clean not only from miners, but also from any viruses in general:
- Avoid using pirated programs - keep in mind that a license protection hacker could just as easily insert malicious code into the program. Such cases are not uncommon.
- Choose free, open source and open source programs - this shows that the developer is not hiding anything. For example, if you need an archiver, install the free 7-Zip instead of the paid proprietary alternatives.
- Download programs only from the official websites of their manufacturers. Never use software collection sites - they often add additional programs and browser add-ons, and sometimes viruses.
- Update programs regularly, starting from operating system, and ending with the smallest utility. Sometimes a small error in a small program is enough for a virus or Trojan to enter the system.
- The Internet is a high danger zone. With the help of a set of browser add-ons and several programs, you can protect yourself well from hacking, infections, and personal data leaks. Explore articles on this topic.
Best wishes! 😉
Also on the site:
New-fangled miner viruses: how to find and remove them updated: March 5, 2018 by: alex ferman
A hidden miner is a virus program that uses your computer's resources to . This is done automatically without the user’s knowledge or any warnings.
Most often, you can catch a hidden miner when downloading files from unverified sources. Usually this is some kind of pirated content that is very popular among users. You can also stumble upon a similar virus when receiving various spam mailings. In any option, you get what you want, and at the same time a hidden miner or utility can be downloaded to your computer to automatically download it from the Internet.
Why is a hidden miner dangerous?
The miner forces your PC to operate at the maximum level of performance, which means that even when performing simple office tasks, the computer can be quite slow. Long-term work at the limit of its capabilities will sooner or later affect the hardware.
First of all, the video card, processor, RAM and even a cooling system that simply cannot cope with daily stress tests.
The first sign of the presence of a miner is braking at simple tasks and a non-silent cooler.
Also, miners may well gain access to your personal information stored on your computer. Here, everything can be used: from simple photographs to data from various accounts and electronic wallets. And this is already very dangerous.
How does a miner manage to hide?
Typically, a separate service is responsible for the operation of the miner on your PC, which allows you to hide and disguise the threat. It is this satellite that controls the autorun and behavior of the virus, making it invisible to you.
For example, this service can pause the work of the miner when launching some heavy shooters. This allows you to free up computer resources and give them to the game so that the user does not experience slowdowns or drops in frame rate. Once the shooter is closed, the virus will start working again.
The same maintenance service is able to track the launch of system activity monitoring programs in order to quickly disable the miner by unloading it from the list of running processes. However, especially dangerous viruses may even try to disable scanning tools on your computer, eliminating detection.
How to detect a hidden miner
If you start to notice that your computer is starting to slow down and get hot, the first thing you should do is run an antivirus scan with the latest databases. In the case of simple miners there should be no problems. will be detected and eliminated. You will have to tinker with viruses that hide their presence well.
Systematic monitoring of the Task Manager, which on Windows can be opened using the key combination Ctrl + Alt + Del or Ctrl + Shift + Esc, will allow you to track hidden miners. For 10–15 minutes, you just need to observe active processes with complete inactivity. Close all programs and don’t even move your mouse.

If, in such a scenario, one of the active or suddenly appeared processes continues to load the hardware, this is a good reason to think about it. The origin of such a process can be checked using the “Details” tab or through an Internet search.
Many hidden miners that mainly use PCs may not load the central processor, which means they will not appear in the Task Manager on older versions of Windows. That is why it is better to assess the load on the hardware using specialized utilities such as AnVir Task Manager or Process Explorer. They will show much more than the standard Windows tool.
Some miners are able to independently disable the Task Manager a few minutes after it starts - this is also a sign of a potential threat.
Separately, it is worth highlighting the situation when the “Task Manager” demonstrates excessive load on the processor from the browser. This may well be the result of a web miner operating through a specific website.
How to remove a hidden miner from your computer
The first and most logical weapon in the fight against such a scourge is an antivirus, as already mentioned above. However, miners are often not recognized as malicious threats. At most, they are considered potentially dangerous, especially if they came onto the computer along with a pirated game or a hacked program.
If you do not have a powerful antivirus, you can resort to the help of small healing utilities. An example is Dr.Web CureIt! , which is often used to search for hidden miners. It is distributed free of charge.
Manually, without any third-party tools, removing the virus is also possible, but you must be 100% sure that it is the miner that you have detected. In this case, you need to go to the registry by typing regedit in Windows search, and in it, use the Ctrl + F key combination to launch an internal search (or through “Edit” → “Find”).

In the line that opens, enter the name of the process from the dispatcher behind which, in your opinion, the miner is hiding. All detected matches must be deleted through the context menu. After this, you can restart the computer and evaluate changes in the load on the hardware.
Conclusion
It is important to understand that a hidden miner is dangerous not only because of its excessive load on the PC, but also because it can intercept your personal data. At the first hint of such a threat, run a deep scan of your computer’s memory with a current antivirus.
Don't forget that your computer can slow down for a variety of reasons. More important feature The threat of hidden mining is excessive PC activity during idle time or when performing basic tasks. Pay attention to the operation of the video card coolers: they should not make noise when there is no load.
If you do find an unknown process that is loading your computer to capacity, you definitely need to deal with it. Using anti-virus software or manually, finding and deleting it through the registry.
Hi all. Today I will talk about virus miners. What is this? Where can you catch them? What will happen to the computer if it is infected with a miner? How to get rid of the miner virus?
What is a miner virus?
This is a virus that uses your computer's computing resources to earn cryptocurrencies. That is, the scammer, using the resources of your computer and your electricity, earns real money! A lot of computers are now infected with this virus, most of the computers that are brought to our service are now also infected with the miner virus and users do not even know that they are infected. There are hundreds of thousands or even millions of such computers, imagine how much the owner of such a virus earns. By the way, in one of my videos I showed how you can make money yourself - mine cryptocurrencies on your PC.
Mining on a home computer
It’s very easy to catch a miner virus now, and here’s where you can catch it:
Downloading programs from dubious resources
Previously, so-called additional software was built into programs, so that all sorts of crap would not be installed on the computer, you had to carefully perform the installation and uncheck all the boxes that, without your permission, could install additional, often malicious software on the computer, I think everyone remembers this. Nowadays, mining software is also built into the program installer. Sometimes when installing a miner virus, you will not even see a message about its installation. The miner will install itself without your knowledge or demand. To prevent this from happening, be sure to use an antivirus, download programs only from trusted sources and carefully follow all the checkboxes when installing additional software or use the Uncheky program. And as I have said many times, all files should be checked through the virustotal website.
Downloading pirated games
Just the other day they brought us a computer, the computer was serviced by us, the owner complained that the game, which previously produced 100 FPS, began to produce 20-30 FPS, although the computer hardware did not change, neither did the drivers or Windows. The person installed more new version games by downloading it from a torrent, the so-called repack. We started checking and found out that with a sufficiently powerful computer, the game loaded it 100%. The entire processor and video card were loaded. We started looking for the reason for this activity and it turned out that along with the game the person installed a miner virus. It worked extremely cunningly, only during the game and it was very difficult to understand that the miner was loading the PC, because the game also puts a load. Most likely, the scammers were simply greedy and set the miner settings to too high a percentage of the load on the card and percent. If this percentage had been lower, the owner would not have noticed that his computer was infected with a miner virus. Have your games started to glitch that used to work fine? Maybe it's a miner! And you can search for such cases on the Internet yourself.
Just by visiting your favorite website
The story is funny and how it touched my site. My site has several moderators who monitor the site and respond to comments. So, one of my moderators installed a code on the site that starts cryptocurrency mining directly through your browser without your knowledge or permission. You only need to open any page of the site. All your processor works for the site owner. Of course, everything on my site has already been corrected, and the moderator went into everything famous place. Want to see how it works? I created a separate one on which I left this script. By the way, if you want to help my project, you can open this page and your computer will work for me). And I have already noticed such a mining script on many sites where you can watch a movie or series, this is how site owners monetize their sites. Many people install adblocks and sites become unprofitable, this the only way making money on the site.
What will happen to the computer if it is infected with a miner?
It's simple, your computer will always work at maximum load. This can cause the equipment to overheat and fail; if you do not monitor the temperature, I recommend monitoring the computer temperature through the program. Also, at a constant elevated temperature, computer parts will have a reduced service life. Under constant load, the computer will consume a lot of electricity.
How to get rid of the miner virus?
Everything is very simple I have it good video To remove all viruses from your computer, this will suit you:
Remove all viruses from your computer
Just clean your computer and be on guard in the future!
Well, what to do with sites that have a miner script? You need to install a plugin in your browser that disables JS on websites. For Chrome-based browsers this plugin is Tampermonkey, and for Firefox it is NoScript. Install the add-on and disable script execution on unwanted sites.
I present to your attention my video




